|
Unconditional security: One-time PAD based on Wireless Entanglement Amir
K. Khandani
Every day, we create 2.5
quintillion bytes of data — so much that 90% of the data in the world
today has been created in the last two years alone [1]. It is predicted
that the amount of traffic flowing over the internet will reach 667 EB
(EB=1018 Bytes) annually by 2013, accounting for about 0.2
megabytes/sec/person (7B population, 24hours) [2]. Wireless access
plays an important role in this growth. The increased use of data
services has been accompanied by a new set of cyber threats which are
developing in ever more sophisticated ways. This has posed many news
challenges to guarantee data security. Motived by this urgent need,
there has been extensive research to explore new methods for security,
including Information Theoretic Security and Quantum Cryptography. In
spite of all the attempts, and although there has been significant
progress on the theoretical aspects, these new approaches are still far
from practice. The only applicable method of security is currently
based on computational complexity which means encrypted data is not
really secet, it is just difficult to guess. With the ever increasing
computing power and sophistication of hackers, these conventional
approaches will be soon obsolete. This presentation introduces a novel
practical approach to provide unconditional security based on using a
two-way wireless channel to establish a secret key (one-time pad)
between two legitimate parties. Two-way wireless enables providing a
reference of phase between the two legitimate parties which in turn is
used to extract a common phase value. Each such phase value can
completely mask a phase-shift-keying (PSK) symbol (zero information
leakage). The shared phase depends on the propagation enviroemnt
between legitimate parties and will be impossible to guess even by an
eavesdropper who is in close vicinity, has unlimited processing power
and enjoys high signal-to-noise ratio. Two-way link in essnease
provides a wireless entaglement between legitimate parties. Thereby,
this method is called Wireless Entanglement Security (WES). Unlike
methods based on Information Theoretic Security or Quantum
Cryptography, the proposed WES approach can correct for possible
mismatches between common phase values as part of the underlying error
correction scheme used for data transmission. In addition, this
presentation introduces methods to perturb the wireless channel such
that a number of such common phase values can be generated, together
providing a longer secure key.
[1] Martin Hilbert and Priscila López, "The World’s Technological Capacity to Store, Communicate, and Compute Information", Science 2011 [2] Gartner Press Release, 27 June, 2011 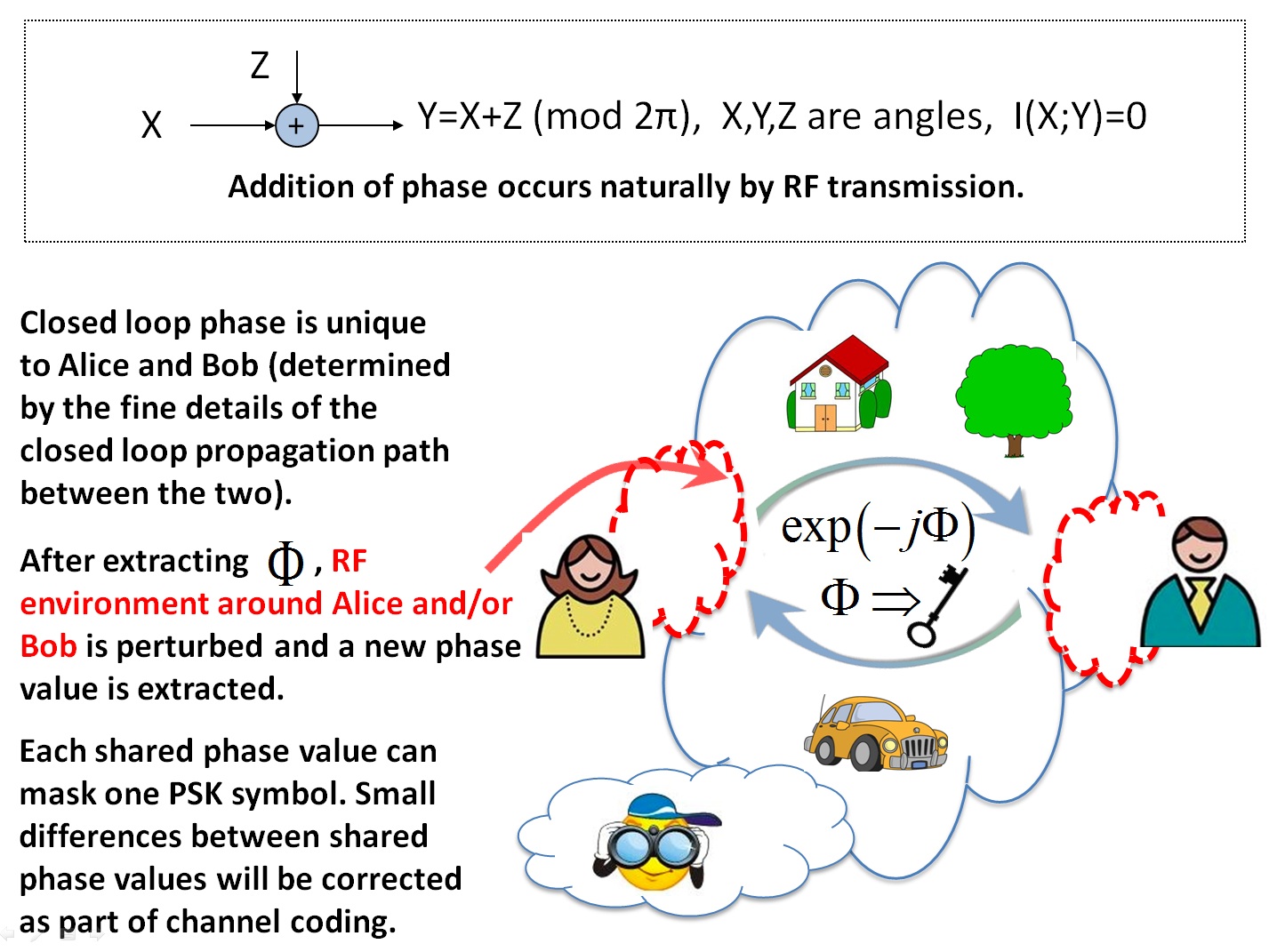 |